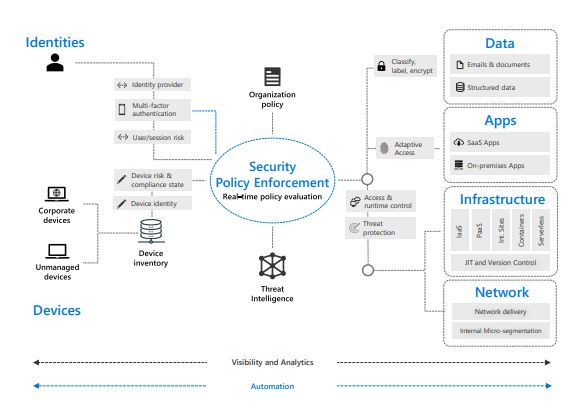
Last month the National Crime Security Centre (NCSC) updated their Zero Trust principles. Zero Trust is not a piece of technology, but rather it is a framework that is built on the assumption that all devices and systems, even those within the network perimeter, are already compromised.
Microsoft and NCSC Zero Trust models have many common themes and foundational elements including identities, devices, applications, data, infrastructure, and networks, etc. As experts in delivering secure, resilient cyber and information services, we have adopted and implemented Microsoft Zero trust Security architecture model to address our customer’s security challenges, as companies have been forced to move large numbers of users to remote working this year. The result of this has seen a significant impact on the way organisations now operate, accessing work-cloud environments using approved, and unapproved, devices that may not be as secure as you would like.
There are two pieces of reading that I recommend when starting your journey:
For more information on this, please feel free to speak to me at cyber@methods.co.uk. You can also find out more about our cyber security services here.
Gareth Jones is Group Chief Information Security Officer at Methods.