Defending against HTML smuggling
Methods’ Group security and risk consultants from CoreAzure and Methods BDT have been engaged with a major global UK public sector organisation to provide security operation center (SOC) services, and have recently been defending against a sophisticated HTML smuggling campaign. The SOC team investigated this as part of a wider phishing campaign in which targeted users were sent malicious files imitating a legitimate business process in an effort to gain access to the organisation’s environment.
A total of 77 HTML smuggling emails were detected, of which 17 users reported these as suspicious. Of the 77 malicious emails detected, the SOC team only received 15 high severity from Azure Sentinel.
Further research found the method used by the threat actor(s) was HTML smuggling. The HTML smuggling method is highly evasive as it can bypass standard perimeter security controls such as web proxies and email gateways, which only check for suspicious attachments like EXE, ZIP, or DOCX.
Below is a graph showing the trend of emails delivered which were recognised as phishing emails.
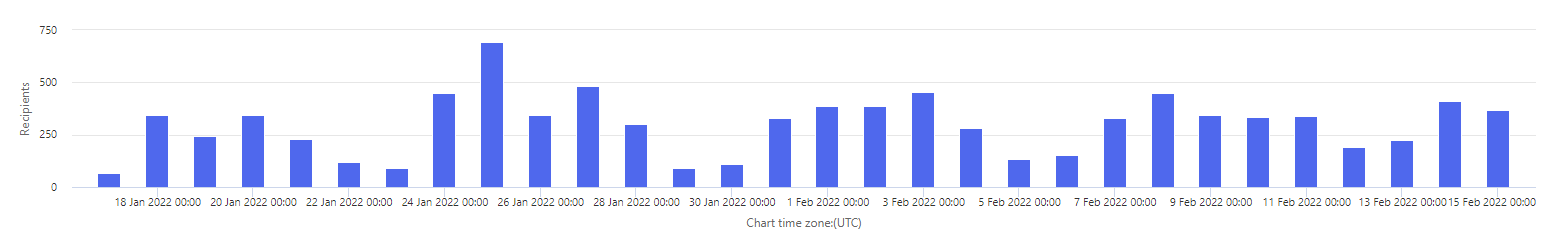
Figure 1 depicts ‘recipients’ on left hand axis against the ‘chart time zone (UTC)’
The main purpose of this style of attack is to install malware code, Trojans, spyware etc. to gain access to an organisation’s environment.
HTML smuggling is a malicious technique used by threat actors to hide malware in an encoded script in a specially crafted HTML attachment or web page. The malicious script decodes and deploys the payload on the targeted device when the victim opens the HTML attachment. The HTML smuggling technique leverages legitimate HTML5 and JavaScript features to hide malicious payloads and evade security detections and generate malicious files behind the organisation’s firewall. Microsoft researchers stated this technique was observed in a spear-phishing campaign by the infamous NOBELIUM.
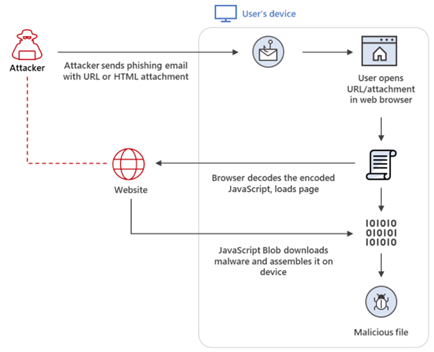
Figure 2. HTML Smuggling Overview – Microsoft
Specifically, HTML smuggling leverages the HTML5 “download” attribute for anchor tags, as well as the creation and use of a JavaScript Blob to put together the payload downloaded into an affected device.
HTML smuggling presents challenges to traditional security solutions. Effectively defending against this stealthy technique requires defence in depth. It is always better to thwart an attack early in the attack chain—at the email gateway and web filtering level. If the threat manages to fall through the cracks of perimeter security and is delivered to a host machine, then endpoint protection controls should be able to prevent execution.
It may not be straight forward to defend against this method of attack due to the wide use of JavaScript and the way it is utilised throughout an organisation’s environment. It is almost impossible to identify malicious JavaScript as it flows down the wire as the same JavaScript code which can be obfuscated in many different ways, and therefore content or signature matching will be challenging to do. In addition, many legitimate JavaScript frameworks make use of obfuscation techniques in order to minimise file sizes and improve the speed of web applications, so simply blocking obfuscated JavaScript is not really an option either.
Microsoft 365 Defender Threat Intelligence Team recommend that Endpoint security teams should be looking for:
- JavaScript or VBScript from automatically running a downloaded executable file
- running potentially obfuscated scripts
- executable files from running “unless they meet a prevalence, age, or trusted list criterion”.
The SOC team suggested the following remediation steps to the organisation impacted (provided by Microsoft) to mitigate the risk of HTML smuggling:
1.
Ensure Safe Links and Safe Attachments are implemented to provide real-time protection against HTML smuggling and other email threats. Specifically check for the following to detect malware-smuggling HTML attachments:
– An attached ZIP file contains JavaScript
– An attachment is password-protected
– An HTML file contains a suspicious script code
– An HTML file decodes a Base64 code or obfuscates a JavaScript
2.
Ensure attack surface reduction rules block or audit activity associated with HTML smuggling.
The following rules can help:
– Block JavaScript or VBScript from launching downloaded executable content
– Block execution of potentially obfuscated scripts
– Block executable files from running unless they meet a prevalence, age, or trusted list criterion
3.
Prevent JavaScript codes from executing automatically by changing file associations for .js and .jse files. This would certainly prevent the HTML smuggling, however, Javascript is indispensable for BC and therefore not a practical solution.
4.
Check Office 365 email filtering settings to ensure they block spoofed emails, spam, and emails with malware. Use Microsoft Defender for Office 365 for enhanced phishing protection and coverage against new threats and polymorphic variants. Configure Office 365 to recheck links on click and neutralize malicious messages that have already been delivered in response to newly acquired threat intelligence.
5.
Check the perimeter firewall and proxy to restrict servers from making arbitrary connections to the internet to browse or download files. Such restrictions help inhibit malware downloads and command and control (C2) activity.
6.
Turn on network protection to block connections to malicious domains and IP addresses.
7.
Turn on cloud-delivered protection and automatic sample submission on Microsoft Defender Antivirus. These capabilities use artificial intelligence and machine learning to quickly identify and stop new and unknown threats.
8.
Educate users about preventing malware infections. Encourage users to practice good credential hygiene—limit the use of accounts with local or domain admin privileges and turn on Microsoft Defender Firewall to prevent malware infection and stifle propagation.
If you would like to talk to our security experts or find out more how Methods could help you, please contact cyber@methods.co.uk.