Methods worked with a central government organisation to develop a unified security ecosystem which would detect, respond to, and recover from critical threats – fast. Many of the clients’ toolsets were configured ‘out of the box’ without customisation or line of sight linking the products together, this left alerts open for weeks with the potential to cause significant damage to the business.
Methods developed a fully configured environment capable of monitoring and reacting to threats and breaches, and reducing residual risk to the organisation. At the start of September – having delivered this holistic view of the organisations’ current threat landscape and implemented complex security signals and alerts – we were immediately alerted to activity by an active threat group named DEV-0856. The team were able to isolate the machines affected whilst investigations were carried out.
The incident was instantly assigned a ‘high severity’, but with the quick reactions of the team, the incident was reassigned as ‘medium severity’ to the business as many security operational procedures had already been undertaken.
The threat was later identified as the ‘Raspberry Robin’ malware, which was spreading via infected USB devices through a group called TANTALUM – an emerging threat group that has been observed targeting NGOs, telecommunications providers, government, and military sectors in Africa, South East Asia and countries neighbouring China. Their preferred techniques include deployment of malware (usually PlugX) to Windows networks through infected USB storage devices and persistence established using scheduled tasks. In addition to malware, the group also operate with stolen credentials to access email and other network resources belonging to the victim. This group is publicly referred to as MUSTANG PANDA (Crowdstrike) and BRONZE PRESIDENT (Secureworks).
Worryingly, whomever successfully launched Raspberry Robin has yet to exploit the infiltrated Windows networks. Microsoft has identified Raspberry Robin as a high-risk campaign, and there does not seem to be any mitigating strategy other than avoiding putting suspicious USB devices into a Windows network.
Attackers could easily escalate their attacks given that the malware can bypass User Account Control (UAC) on infected systems using legitimate Windows tools.
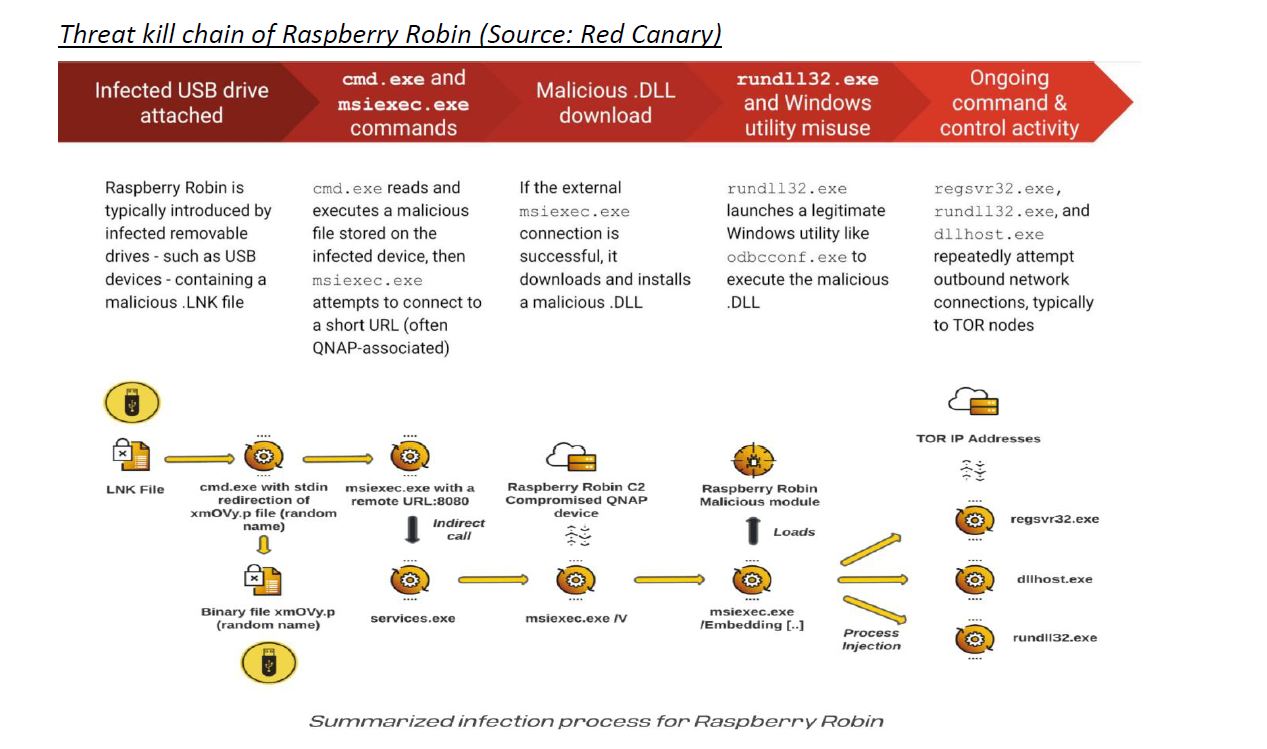
So far the actions taken by the CoreSOC team, workplace team, and the desktop team have mitigated the risk of the threat spreading across the organisations environment by isolating the machines that were impacted. Our client needs to remain vigilant about the use of USBs as we believe there could be further activity (such as ransomware) from the threat group who will be persistent in their efforts to cause damage. The organisation must now re-evaluate the use of USBs, and how users are freely allowed to use them to download/upload content in the delivery of their work, to protect against this type of threat to the organisation in the future.
Our biggest question and concern always remains the same…. What are the operators objectives…..?
If you would like to know more about protecting your organisation from ‘Raspberry Robin’, or to find out more about how we can help keep your systems and data safe, please contact us at cyber@methods.co.uk.